Developer-Led Landscape: Software Supply Chain Security
The software supply chain contains anything that — if disrupted — impacts business continuity. Securing it will be a top 3 CISO concern and $7B ARR market by 2030.
Previous Developer-Led Landscape Papers
Developer-Led Landscape: Complexity, Automation, and Autonomous Development
Developer-Led Landscape: Some 2022 Predictions
Developer-Led Landscape: 2021 Edition
Developer-Led Landscape: Latency-Optimized Development
Developer-Led Landscape: 2021 Trends Foretell New Approaches To DevOps
Developer-Led Landscape: Cloud-Native Development
Developer-Led Landscape: The Original
A copy of the database listing all of the products we track is available in a public Google sheet.
About Dell Technologies Capital
We are investors, and if you are in a developer-related business, I’d love to connect.
We lead investments in disruptive, early-stage startups in enterprise and cloud infrastructure. Entrepreneurs partner with us for our deep domain expertise, company building experience, and unique access to the enterprise ecosystem.
We have 72 active portfolio companies, 72 exits, 9 IPOs, and 12 unicorns. We invest ~$200M per year.
We have 6 investments that are part of the Secure Software Supply Chain - a profile on each is available at the end of this article!

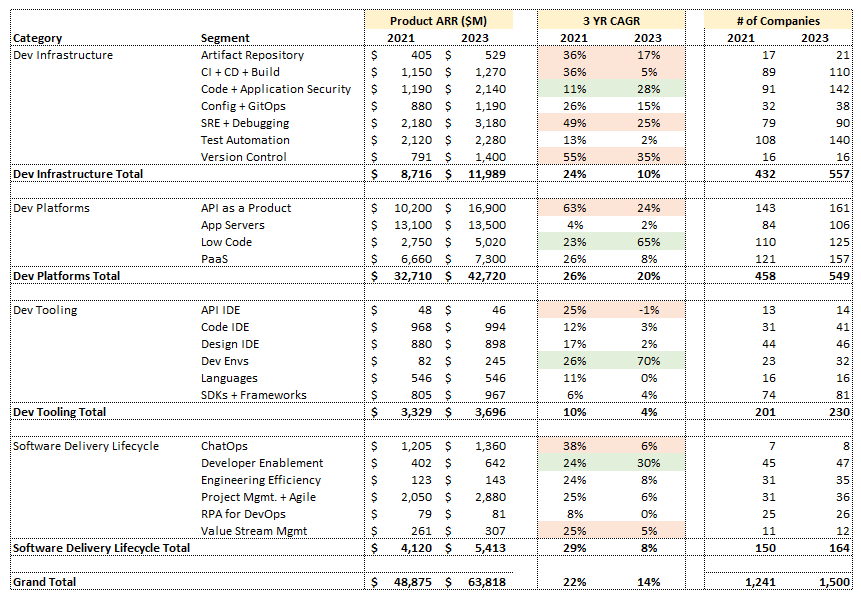
1.0: The Developer-Led Landscape In 2023 Is $64B ARR Driven By 1,500 Companies.
1.1: The Developer Market Had Its First Year Of Declining Growth Since 2009.
The first version of this landscape was drafted in 2009 and contained 95 companies.
This is the first time where their collective growth rates have dropped below 20%.
The drop wasn’t subtle, having consistently been growing 25% for many years.
This year's drop in growth to 16% reflects many challenges the industry is facing:
Earnings recession causing many organizations to look at efficiency initiatives which places limits on capital that can be used to purchase additional tools and platforms.
Efforts by companies to rein in cloud spend, which directly impacts total spend considered on dev runtime platforms (see Hey’s public decrying of cloud costs and decision to repatriate their cloud stack to on-prem).
Complexity and fragmentation that naturally occurs from having so many competitors materialize in these categories.
Tech organization layoffs that have begun to shift the power dynamic away from software developers (higher salaries, only work with tech they prefer, resisting corporate policies) back into the hands of hiring organizations, which can standardize practices and tools limiting vendor selection and total spend.
1.2: Automation & Efficiency Outperform The Broader Market And Drove Significantly Higher Growth Especially Versus Pre-Recession.
The segments whose growth rates have been increasing:
Code + Application Security. You cannot ship insecure software, and with the amount of code being generated, the need to incorporate automated forms of application security has exploded causing the sleepy app sec segment to grow at its fastest rate in two decades.
Low Code Platforms. A huge uplift in growth rate has happened as organizations look to enable non-technical knowledge workers with the ability to create and maintain applications and services using opinionated techniques with low training.
Developer Environments. Growing off of a small base, the automation of developer environments as part of commits, pull requests, features, and branches has looked to automate away one of the biggest challenges developers have faced for 50 years: “it worked ok on my machine.” Repeatability, reproducibility, and instantaneous access has caused a large number of new entrants to appear chasing a trinity of nearly impossible expectations.
Developer Enablement. Programs and creative software that help development teams become more productive: education, community, conferences, knowledge management, and metadata repositories.
1.3: 83 Acquisitions Of Developer-Led Landscape Companies Over 18 Months - The Fastest Pace Seen In Over A Decade.
During the 2021 era, we were tracking up to 20 acquisitions, or about 1.5 / month. We are tracking closer to 6 acquisitions / month now.
Of the 83 companies, 60 had ARR <$5M, reflecting the likely scenario that these acquisitions were small dollar or equity exchanges.
The largest (by ARR) acquisitions made over the past few quarters includes Applitools, Buildbox, SocketLabs, experitest, Artifex Ghostscript, Kiuwan, Imvision, Gatsby, Puppet (rumored at only 3x ARR), Remediate, QA Systems, Tasktop, Telerik, Froglogic, AppGyver, Pathwire, and Whitehat.
Some of these acquisitions happened before the most recent publication, indicating that they had occurred, but we missed recording them in the database. Even so, without those acquisitions, the pace of acquisitions would still be the highest recorded.
1.4: 53 Companies Went Bankrupt Or Out Of Business - The Largest Number Ever Seen For The Developer-Led Landscape.
These companies raised $63M in capital from VCs and angels. Bankruptcies are strong signals indicating lack of interest in a category or potential team weakness as these businesses were unable to acquire sufficient customers or attract a strategic buyer willing to pursue an acquihire or asset purchase.
The companies who had raised the most VC money that are no longer operating include Conducto, Flynn, Kite (particularly interesting since they were a pioneer in AI-generated code completion prior to GitHub Copilot), Syncano, Toolchain, and Up9 (also interesting as the founders had previously built the very successful Blazemeter).
1.5: Peak(ing) DevOps - This Landscape Added 213 Businesses Who Have Collectively Already Raised $2.14B In VC!
In the last installment of this landscape, I suggested that we are reaching Peak DevOps, and that the landscape would likely reduce by more than 500 companies from those that could not raise sufficient venture backing, driving their revenues high enough to create a sustainable cash flow positive business, or be rejected by customers as consolidated platforms rise in maturity.
Well, we certainly haven’t peaked, with 136 companies exiting due to bankruptcy or acquisition, yet 213 new companies added in the same period, the landscape has grown rather than shrank with new VC-backed businesses outpacing those that are leaving.
So, maybe more of a Peak”ing” DevOps rather than Peak DevOps?
What’s stunning is the amount of total VC raised by brand new entrants. Of the 213 companies added, 162 raised $2.14B in VC money after they were formed. That is a stunning average of $13M in total VC raised for each new entrant. Even more remarkable is that most of this money was raised during an earnings recession and VCs becoming more restrictive with their capital allocations.
Now, our research collection philosophy isn’t perfect. We add names to the database when they are brought to our attention, so there can be a lag between when the company was initiated and when we added it to the database. It’s possible that a number of these new entrants were formed and raised during the 2021 hype cycle but did not come to our attention until recently.
The startups who have raised more than $20M shortly after forming are a reflection of where the market is shifting towards: automation, efficiency, consolidation, application security, and autonomy.

2.0: Software Continuity Is Business Continuity.
Software is now core to how companies deliver offerings and provide competitive advantages.
A business’ ability to build, maintain, improve, and operate software systems defines the market’s perception of whether a company is a going concern!
Whether software is your company’s product, or whether it is the mechanism by which employees, customers, and partners engage with your company, any interruption to its continuity will disrupt your business’ operations.
Continuity manifests in many ways:
A SAAS or hosted API that is unavailable or with degraded performance will halt business operations.
A vulnerability in production or published software opens new threat vectors exposing sensitive systems and data.
A pipeline change breaks the build blocking new versions right before a regulatory update (such as February 1st when tax documents must be distributed).
Stolen developer credentials grant unauthorized access to core IP and build systems.
High developer attrition due to tool chain complexity and internal cultural friction creates a knowledge vacuum that slows new releases or, worse, requires massive time to correct a real-time outage incident.
2.1: Software Supply Chain: The People, Process, And Technology Used To Create And Maintain Software Systems.
Most companies define the software supply chain constrained to the pipeline of systems used to build and ship software.
This definition is not broad enough.
The software supply chain contains anything that — if disrupted — will impact continuity.
Whether a disruption is minor or major, any alteration to continuity of the software system fits within the supply chain.
The supply chain, therefore, contains each system, step, and person involved with the software pipeline.
The supply chain is not static - itself a digital animal whose heartbeat reflects the repetitive drum of new code being written, tested, shipped and monitored. Like any organism, failure to maintain the supply chain will lead to its own eventual degradation and failure.
A non-exhaustive list of software supply chain components includes:
The software developers, testers, SREs, PMs, operators, security engineers, architects, designers, and managers who have contributed to a change.
The contributors and maintainers of open-source software (OSS) packages included in software.
The users of a software system, who gain utility from the software, but also through their engagement provide feedback and data which subsequently makes the software better.
The SDLC tooling used by anybody including everything from ChatOps, email, issue management, version control, build systems, testing frameworks, CI/CD/GitOps, monitors, debuggers, APM diagnostics, IDE, IDE plugins, StackOverflow, and AI assistants.
The software platforms which configure and run software. This includes a broad range of infrastructure for which software depends at runtime, though we generally focus on those layers that rest above infrastructure. This includes PaaS runtimes, low code runtime environments, developer virtualized environments like Linux containers, SDKs and frameworks with runtime behaviors such as Next.JS, and programming languages (they have runtimes too!).
Third party service providers, such as those who deliver APIs for which applications depend on.
The financial controls and mechanisms used to pay the people who build the software systems, pay the vendors for which components power software, and receive funds from customers that consume the software.
The organizing principles which enable diverse constituents participating in the construction and usage of software to interact, communicate, and share information. If you want to see someone’s eyes grow wide with concern, suggest that the bi-weekly sprint cadence be altered to 13 days for a single week.
The value system embraced and championed by a software’s publisher which is core to growing community, recruiting new contributors, hiring employees, limiting attrition, and drives vision alignment for future improvements.
2.2: The Software Supply Chain Contains Increasingly More Suppliers, Each With Their Own Supply Chains.
A supplier’s reliability factors include technological, behavioral, and economics.
These supply chains are both internal and external. Since an issue with a dependency can impact what happens with your supply chain, the security of both my supply chain and those of my suppliers is increasingly my own concern.
Vendors are increasingly requiring more stringent reporting, auditing, and standards compliance in terms of how they develop and publish their software. This has become apparent with the explosion of Software Composition Analysis (>$1B ARR) vendors and also the emergence of vendors who focus on analyzing the business viability of 3rd party software suppliers, such as those who host APIs.
Gaining confidence in the supply chains of your providers is becoming as important as securing your own chain.

2.3: A Software Supply Chain Disruption Is A Security Issue.
Disruptions to the software supply chain now inflict numerous kinds of damages:
Business Impact: Downtime driving lost revenue, SLA breaches are a cost due to customer-required compensation, poor experience drives poor productivity and higher COGS from a larger customer experience spend.
Cyber-Security Concerns: Breaches that drive cyber premium increases, compliance breach fines, data theft, and reputation injury.
Personnel: Repeated issues drain morale and sap energy of critical team members, security issues detract from developing software that drives customer value, and unsustainable software systems stymie the intellectual growth of contributors.
There are no two ways to cut the issue - any disruption to the software supply chain is a business continuity disruption.
The safety and continuity of the software supply chain is a security issue.
2.4: The Frequency Of Breaches Tied To The Software Supply Chain Is Increasing In Both Frequency And Consequence.
A breach is defined within NIST SP 800-53 as, “The loss of control, compromise, unauthorized disclosure, unauthorized acquisition, or any similar occurrence where: a person other than an authorized user accesses or potentially accesses personally identifiable information; or an authorized user accesses personally identifiable information for other than authorized purpose.”
2.4.1: The Top 12 Breaches Of All Time Have Cost $3.5B Just In Penalties.
Yikes, being a CISO may not be the most glamorous job in tech.
2.4.2: Secure Software Supply Chain Breaches Expose Leakiness And Unexpected Attack Vectors.
As of June of 2023, there has been 607 recorded breaches compromising more than 450M data records, a number of which were due to compromises in the software supply chain.
Some recent breaches include (many thanks from the Archipelo team who helped organize these):
Vulnerability Exploit: OpenAI has revealed that the vulnerability in the Redis open-source library, which ChatGPT uses, has led to certain users being able to access the titles of chat logs from another active user. Furthermore, in some cases, these users may have also been able to view the first message of a new conversation, but only if both parties were simultaneously active on the chatbot.
Data Leak: Samsung workers unwittingly leaked top secret data whilst using ChatGPT to help them with tasks. The company allowed engineers at its semiconductor arm to use an AI writer to help fix problems with their source code. But in doing so, the workers input confidential data, such as the source code itself for a new program, internal meeting notes data relating to their hardware.
Malicious Code Injection: Aaron Mulgrew, a Forcepoint security researcher, recently shared how he created zero-day malware exclusively on OpenAI’s generative chatbot. While OpenAI has protections against anyone attempting to ask ChatGPT to write malicious code, Mulgrew found a loophole by prompting the chatbot to create separate lines of the malicious code, function by function.
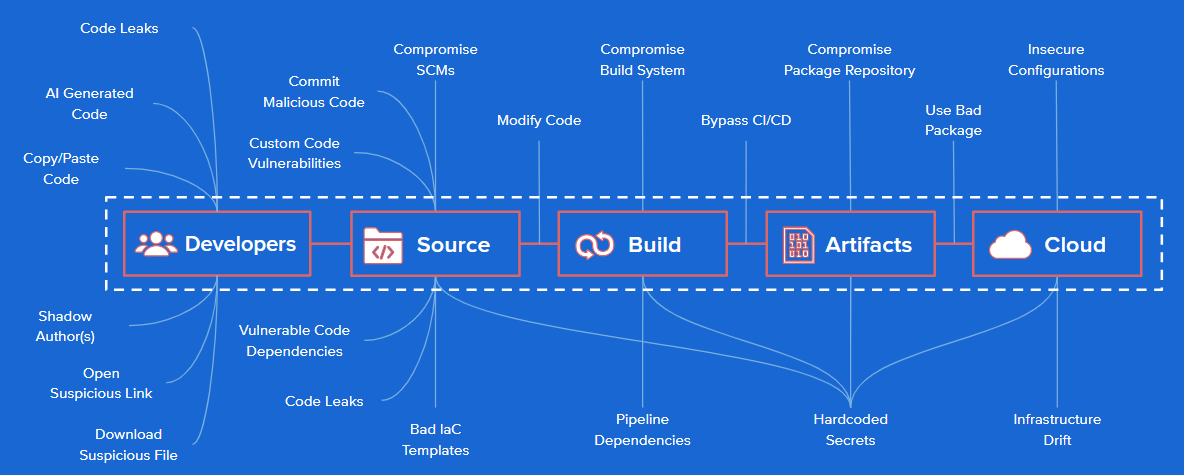
Submit Unauthorized Change To Source Repository: A contractor for SushiSwap with code repository access pushed a malicious commit redirecting cryptocurrency to themself.
Compromise Source Repository: An attacker compromised PHP’s self-hosted git server and injected two malicious commits disguised as commits from legitimate maintainers.
Build From Modified Source Not Matching Source Repository: An attacker modified the build infrastructure of Webmin to use source files not matching those in source control.
Use Compromised Dependency: An attacker added an innocuous dependency and then later updated the dependency to add malicious behavior. This is an example of something seemingly safe at the time of initial inclusion that later becomes unsafe.
Compromised Build Process: The infamous SolarWinds attack was due to a compromised build platform where the attacker installed an implant which inserted malicious code during each build.
Upload Modified Package Not Matching Build Process: The CodeCov attacker used leaked credentials to upload a malicious artifact to a GCS bucket, from which users were downloading directly. A new kind of “man-in-the-middle” attack vector.
Compromised Package Mirroring Repository: Researcher ran mirrors for several popular package repositories, which were compromised to deliver malicious packages.
Typosquatting Package Names: An attacker uploaded a malicious package with a similar name to the Browserify original, playing on people’s misuse of a name to gain access.
2.5: The Secure Software Supply Chain Will Be A Top 3 CISO Issue Within 5 Years And A Top 5 Spend Category Before 2030.
Securing the software supply chain will need to become a $5B market for it to be a top 5 category within the developer-led landscape.
It is already one of the fastest growing segments at 32% annually, growing on a substantial base of $2.14B of revenue.
Interestingly, if I were to slice the landscape slightly differently, it could be argued that supply chain security is already significantly larger than $5B!
Gitlab, for example, is approaching a $400M run rate and included within version control, but arguably most of their revenues are driven by security capabilities included within premium purchase tiers. If Gitlab gives away version control or developer-related features at a low cost, are they still a version control company or a security company? There are more than 100 companies within the developer landscape that could get similar treatment (cough, cough, JFrog, Sonatype, Cloudbees, Harness, GitHub, Puppet, Chef, and many of the test automation vendors).
This implies that…
3.0: Every DevOps Company May Already Be A Security Company.
What drove the Gitlab behavior is due to a simple DevOps principle: developer productivity is not a sellable value proposition.
Developer productivity is difficult to measure, and in many cases even more productive teams do not lead to a company finding actual cost savings. Extracting budget for a developer-led landscape tool that promises productivity is the hardest selling motion and should be reserved for masochists and those that like running businesses that grow slowly.
There are only three reasons that organizations buy software supply chain elements:
Mandatory Infrastructure. Storage, compute, and I/O (and their related abstractions that sit on top such as a PaaS) required to run software.
Mandatory Tools. SDLC-related tools that are essential to building, shipping, and monitoring the software that is produced. Mandatory is a slippery slope here and many companies buy non-essential tools, which always leap to the top of the chopping list any time an organization is facing “cost reductions.”
Security. The cost to the disruption of the business poses such a significant actual or theoretical risk, that the cost to purchase security solutions for the software supply chain, while expensive, are increasingly perceived similar to an insurance premium - a necessary drag against operating margins.
Of the three, security has fantastic gross margins. It’s almost always pure software and considered an essential, must have purchase, which has a tendency to be less sensitive to competitive pricing pressures than other categories.
Mandatory Infrastructure is a wonderful place to be as there are phenomenal Net Retention Rate dynamics (consume more infrastructure, buy more infrastructure) though their gross margins face pressure at scale.
Mandatory Tools is only a so-so place to be as they are frequently measured as a fraction of HC spend and when combined with a tendency for the segment to be heavily fragmented creates upper bounds on how much an organization will spend on tools and margin pressures from too-many-competitors.
This is why savvy GTM leaders in the developer-led landscape have increasingly moved their positioning, channels, distribution, packaging, and messaging to align around a security narrative and reaching into the CISO budget.
Along these lines, every DevOps company is increasingly becoming a security company, or may already be one.
DevOps companies are both part of the underlying risk within the software supply chain and its cyber security protection.
3.1: Code & Developers Are The Soft Underbelly Of Software Development Risk.
In many ways the application security testing market, around for 4 decades, was built around the belief that suppliers (such as a 3rd party OSS module) and developers who wrote code do not maliciously create vulnerabilities. The premise was that vulnerabilities generally occurred due to complexity in system behavior which would create pitfalls not obvious to the developer who wrote the code. As system architecture increased in complexity, then the nature of unseen pitfalls increased, requiring application security tools to keep pace.
Net - application security tools increasingly became as complex as the code they were chartered to protect.
This AST tool complexity has increased by orders of magnitude due to the supply chain. The supply chain incorporated 3rd party OSS modules and their transitive dependencies (and their transitives, and their - well you get the point). To further highlight the severity of this issue, Endor Labs inaugural “State of Dependency Management” found that 95% of vulnerable dependencies are transitive!
Additionally, the nature of how software is built and tested has grown in complexity around agile principles, group collaboration with git, and progressive delivery for continuous updates and feedback. This issue is so prescient, that OWASP has taken to drive awareness of this issue by publishing the “OWASP Top 10 CI/CD Security Risks”.
The combination of an increasingly immeasurable number of code components along with a manufacturing system which leverages complex rules to make decisions, has created a massive attack surface area. Not only do creators need to worry about accidentally introducing a security vulnerability, but they must also now worry about whether the code they are analyzing is authentic, un-tampered, and the developer who contributed the code is trustworthy.
3.2: Supply Chain Risk Is Defined By The Trust Profile Inherited From Every Person, Machine, Technology Stack, and Process Used.
Your reputation, and ultimately the scope of the risk surface that a CISO must embrace, is driven by not only the technology you choose, but the people you work with and the processes they use to create software.
3.3: Complexity, Regulations, & Copyright Are Creating Purchasing Urgency Among CISOs and CTOs For Secure Software Supply Chain Solutions.
There has been a recent confluence of events that have CISOs treating security of the software supply chain as a mandate:
SBOM Mandate: US Executive Order 14028 requires software inventories to be automatically generated if they’re to be used in US Federal agencies. These software inventories must be presented to the appropriate agencies by September 14th, 2023. This order effectively declares the software supply chain as a matter of national security.
Secure Software Design Mandate: The US OMB has declared that all federal information systems, organizations, and agencies along with any organization that works with the federal government (i.e., any software company who wishes to sell to the US Govt.) are required to adhere to NIST 800-53 controls and NIST 800-28 guidance. The NIST framework provides a suite of processes and frameworks for businesses to develop, maintain, and improve information security practices. This includes, but is not limited to, the practices that software companies use to create, secure, and publish software.
Being compliant with NIST 800-53 improves their compliance with other regulatory requirements such as PCI DSS, GDPR, HIPAA, FISMA, FedRAMP, DFARS, and IL 2-6.FDA Medical Device Mandate: The US Food & Drug Administration is mandating that all medical devices running software must create and maintain a software bill of materials (SBOM). The FDA will start to enforce this rule on October 1st, 2023.
AI Generated Content Invalidates Copyright. The US Copyright Office has issued guidance that declares any works generated with AI are not Copyrightable. This has a serious impact on the software development industry as Copyright is what grants a software publisher the ability to set and enforce a software license. With AI code authoring solutions like GitHub Copilot being adopted so dramatically, any organization that is shown to have leveraged AI bots for generating code may lose their Copyright against what they believe is proprietary code. This has been one of the reasons why I have advised all of my portfolio companies to prevent their engineers from using Copilot until these issues are resolved (or to purchase Archipelo’s code provenance tracker - see below).
Security Flaws In Code Are Expensive. 50% of the top 25 CWEs are due to the nature of how code is implemented by developers and oftentimes is undetectable by static analysis tooling that runs as part of a build. Solutions that are able to combine static and dynamic analysis to prevent or detect security flaws in code while the code is being authored are increasingly becoming more important to buyers.
High Profile Breaches Expose Soft Underbellies Of How Software Is Developed. The attack surface of the software development environment is very broad. The NIST 800 standard has documented more than 200 potential attack vectors. The attacks on SolarWinds (2020), NetBeans IDE (2020), Kaseya (2021) and Codecov (2021) represent four prominent examples of software supply chain attacks. Gartner believes that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.
With so many mandates, there may be a rush to think that SBOM generation is a general solution. The risk of “SBOM-is-the-answer” is that they turn into compliance checkboxes that don’t actually improve the security posture of the organization. Organizations will need to embrace a comprehensive and holistic approach to software supply chain security (which we will, of course lay out for the studious reader).
With all of these mandates, it’s no wonder that:
4.0: The Software Supply Chain Security Market Contains 145 Companies Generating $2.14B ARR Growing At A Robust 32%.
The broader market has not settled on a definition of the Secure Software Supply Chain.
I’m defining it as the “vendors who work to protect the integrity of the software development supply chain in order to prevent continuity disruptions.”

It is difficult to put a clear box around what is within the software supply chain security ecosystem and what resides within it. A couple of organizing principles that I believe are appropriate:
Anything that threatens the stability or authenticity of code, whether newly authored or imported through a dependency, is inclusive.
Anything that protects the continuity of the tools and processes directly used by software developers, DevOps, product managers, testers, and SREs is inclusive.
Application security testing is a critical part of ensuring new code is safe, but it is not a comprehensive definition (missing many critical parts that help assess how the code is authored).
Solutions that specifically look for issues with how code is moved into production or the behavior of code in production is inclusive, though broad-based production + endpoint security solutions are exclusive (really, where do you create that boundary?!?).
Even with these organizing principles, there are areas where the market has overlap, in many cases because much of this landscape is still being formed:
The product responsible for owning and certifying SBOMs has not yet been defined with SCA, Pipeline Security, and Dev Security Posture Management vendors all providing essential generational inputs to these assets.
Most SAST / DAST / IAST solutions can work with APIs and other assets, muddying the waters between pure play API Security vendors and the role of application security testing.
Many API Security vendors provide both development and runtime protections, with many runtime protections similar to WAF or other endpoint solutions which are generally not inclusive to this landscape.
While there are pure play Secrets Scanning vendors, these capabilities are frequently provided up and down the stack with application security testing and external security vendors doing similar analysis.
Many analysts treat the SCA market as focused on OSS. There are many vendors within the SCA landscape who offer vulnerability remediation to third party software that is not OSS.
4.1: A Secure Software Supply Chain Vendor Has Yet To Make An IPO.
Only $452M of the $2.14B of ARR is attributed to products that are part of publicly traded companies today. This number would be significantly higher if we wanted to treat most of GitHub and GitLab’s revenues as security-driven.
Interestingly, this public company revenue concentration (or really lack thereof) is far below the 66% of ARR attributed to publicly traded company products across the entire developer-led landscape.
Further, by my analysis, there are 20 companies in the secure software supply chain landscape whose product ARR is greater than $25M, and of those there are only two products from publicly traded companies: Synopsys and CyberArk.
The largest vendors in this landscape have been around for as long as 35 years and include reputable and stable security vendors including Sonarsource, Veracode, Snyk, Checkmarx, Sonatype, Mend, and Perforce.
With most of the revenue in this segment attributed to application security testing, having vendors with >$250M ARR, the markets have never believed their role was strategic enough to warrant enough interest to be able to achieve an IPO.
Most of the largest app sec testing vendors are currently owned by PE.
With all software now a critical security risk and as the total secure software supply chain ARR surpasses $5B, this category will be seen as strategic and large, paving the way for new IPO candidates from any vendor that can show potential to consolidate app sec and reach towards $1B ARR.
4.2: Software Supply Chain Security Companies Have Raised $7.4B From VCs and PE.
About half of this money has been from private equity acquisitions within the application security testing segment.
The hottest VC segment has been API Security, of which $1.6B has been raised into these startups, but the collective segment only has $182M ARR. With the concept of APIs being everywhere and most companies designing their businesses as API-first, the need to secure APIs appears to be significant, though the market has not allocated nearly as many purchase dollars to it, especially relative to the expectations that VCs have in order to drive a reasonable return. This segment will need to have $500M ARR collectively before VCs can see liquidity with a 2x step up return.
A similar dynamic is playing out with Software Composition Analysis due to the near constant growth and scale of the OSS ecosystem. This segment is healthier at $438M ARR, giving investors numerous paths to seeing reasonable returns.
4.3: Application Security Testing Is The Largest Segment (And Oldest) Of Software Supply Chain Security Generating $1.6B ARR And Growing 25%.
There are a number of vendors with >$100M ARR including Sonarsource, Veracode, Snyk, GitLab, and Checkmarx. The market has historically been slow growing, but recent urgency to secure software systems has provided renewed and enhanced focus on AST as a strategic platform to build software security.

4.4: Internal Supply Chain Security Is An Emergent Segment With 40 Vendors Spanning Protection Of Developers, Development, Staging, And Production Generating $230M ARR.
Very few solutions in this category existed more than 5 years ago. Most of the 40 companies mentioned are less than 3 years old.
We performed a use case analysis to identify all of the unique capabilities that these new companies are delivering to their customers. They drive both protection (avoiding the introduction of malicious behavior or code) and compliance (proving authenticity & establishing reputation).

4.5: The External Supply Chain Is Large and Growing Larger Due To Prevalence Of Open-Source Software.
We found 30 companies that provide analysis of open-source software (OSS) vulnerabilities within an organization’s supply chain. Most of the large analysts would say that the pure SCA market is inclusive of a small set of vendors, but reality is that many DevOps companies are claiming to provide their own unique insights into the OSS that is pulled into an organization.
Further, the $440M of ARR attributed to SCA are for the pure-play products focused on that form of security analysis. If we included the ARR from package managers and artifact repositories (which are also a huge source of OSS validation), then the total ARR would at least double.
4.6: Early, Limited M&A For Application Security Indicates Large Cybersecurity & DevOps Vendors View Application Security As Strategic.
The gauntlet was thrown down last year when Palo Alto Networks acquired Cider Security out of Israel for a whopping $195M. Cider was a *very* early entrant into the Secure Pipeline segment of this landscape, indicating that PANW’s desire to take a larger share of the CISO budget now has ambitions inclusive of finding a way to provide a comprehensive application security testing and supply chain security solution set. Cider is more akin to a secure software supply chain posture management solution - providing a snapshot of all the pieces contributing to the supply chain but depending upon 3rd parties to provide specialized application security testing, infrastructure, container, or other types of scans.
I would not be surprised to see PANW drop another $1-$3B to pick up critical application security testing vendors in order to compete with Sonarsource, Veracode, and Snyk, especially if the shift-left mindset begins to undermine their CISO-level sell proposition.
Other acquisitions are indicative of early skirmishes as organizations work to establish what their security posture will be for the supply chain indicating strategic intent:
Peach Technologies (fuzzing) acquired by GitLab in 2020.
Deepcode (SAST) acquired by Snyk in 2021.
Cloudskiff (production drift detection) acquired by Snyk in 2021.
FossID (C++ SAST) acquired by Snyk in 2021.
Codiga (SAST) acquired by Datadog in 2021.
Sqreen (IAST-like) acquired by Datadog in 2021.
Crashtest (DAST) acquired by Veracode in 2022.
Enso (ASPM) acquired by Snyk for $50M in 2023.
Blubracket (Secrets) acquired by Hashicorp in 2023.
4.7: The Largest Secure Software Supply Chain Incumbents Are Mostly Private, >$50M ARR, And Private Equity-Backed.
While companies like Contrast and Snyk are VC darlings, there is no other segment within the developer-led landscape that has as many $50M ARR vendors as the secure software landscape. This is due to the multi-decade longevity of application security testing allowing organizations like Veracode and Sonarsource to develop mass along with the massive urgency and potency that came from SCA vendors satisfying the acute OSS issues that appeared.
Further, by our reckoning, at least 40 of the companies in this security landscape have ARR >$10M, nearly 1 out of every 3.5. When compared to the full landscape with 1500 companies, the average is 1 out of 8!
5.0: Will Dev-Led Security Be Next? Shifting Security Left Helps, But Is Not The Answer.
Well, Tyler, your landscape and research has been premised on the concept that there is a new class of buying influencer based upon the ability for developers to influence, adopt or purchase products. It seems like a lot of these solutions are influenced by the CISO, application security professional, or DevOps. Where is the developer-led aspect?
5.1: Shift Left Is A Powerful Phenomenon For SAST, DAST, SCA, And Least Privilege Enforcement.
You’d need to have your head in the sand to have missed the Shift Left phenomenon spearheaded by Snyk, and copied by many marketing departments throughout this security landscape.
The concept of Shifting Security left is to allow developers to address major security issues while they are working within code, hopefully in a format that is complementary or conducive to the existing developer experience they work within (do NOT get in the way of the edit-save-build-test-repeat flow!).
Snyk unlocked this concept because of a once-in-a-decade innovation around how to include certain types of static testing within a part of the everyday dev experience: the pull request. This combination was magical, similar to what I tell my wife about PB & chocolate in Peanut Butter Cups. This was due to the ability to bring certain types of security results into a portion of the flow that allowed a developer to respond with a long asynchronous break awaiting results. And it brought results that were actionable by that developer without having to collaborate with other developers.
It’s because of this magical combination that there are some additional solutions which can also benefit from having immediate developer reactivity: the risk score of a new 3rd party OSS component, some dynamic runtime performance and security analysis of the code, static testing, avoiding accidental secrets exposure, and ensuring that developers only have least privilege access to critical resources from their command line or IDE.
DTC’s investments in AppMap, Bastion Zero, and Endor Labs exemplifies these properties so significantly that most of their adoption does come from developers (in fact, AppMap is approaching 100K installs in the IDE).
Everything else…
5.2 However Shifting Everything Left Misses The Mark.
Unfortunately, what was magical for one aspect of security doesn’t make it a fit for the other parts. And what made Snyk magical for one aspect of development is causing heartburn for others. Snyk pushing everything into the hands of development ends up causing R&D to handle all the issues and can cause the opposite effect - a slowdown in velocity and cadence as development chases down issues unrelated to code.
So what? What’s the right thing for a CISO to do?
5.3: Vendors Claim Comprehensive Supply Chain Security Coverage, But Reality Requires CISOs To Combine Multiple Solutions To Mitigate The Entire Attack Surface.
It will be a challenge for CISOs to sort through the vendors in this landscape. There is a lot of extended promises and vendors who provide overlapping capabilities.
A CISO can attack the most risks with the least amount of vendor overlap by combining 4 solutions deployed holistically:
A Developer Security Posture Management Solution (DevSPM): This will ensure that your developers and the code they produce is signed, has attestations, is authentic (no AI or copy-paste which can invalidate copyright), has context to how code is created for monitoring provenance at the earliest SDLC stages, and:
A Pipeline Security Solution: This will ensure that you are able to run various scanners (infrastructure, container, secrets) across any tool that touches code. This should be integrated with an appropriate IAM tooling or Least Privilege Enforcement solution to ensure that only valid bots and humans are touching code, and:
An App Sec Testing Solution: This should generally encompass a holistic approach that provides SAST, DAST, fuzzing and penetration testing. It should be a solution that works across programming languages and architectures (VMs, microservices, APIs), along with operating across different types of environments from development through production, and:
An SCA Solution: This will provide vulnerability scanning across the maze of open source along with giving your development teams the ability to identify new open-source libraries that they can safely incorporate.
Along these lines, you should consider that…
6.0: Dell Technologies Capital’s Investments Deliver Comprehensive Coverage For Securing The Software Supply Chain.
DTC has made 39 cyber security investments. Over the past few years, we have established 7 investments with vendors that are rethinking the security of the software supply chain, and we expect to make more.
6.1: Archipelo: Verifying Code Provenance With Developer Security Posture Management.
Archipelo provides a comprehensive approach to establishing code provenance and the authenticity of development.
They detect code that is AI generated or copy-pasted, say from Stack Overflow, in order to create a detailed record of code provenance. They have an automated Code Provenance Tracker that identifies non-provenanced code within your code base, and then gives application security, DevOps and software engineers an attestation engine to validate the authenticity of code that is part of a release.
Archipelo is able to monitor and prevent code leakage with their Code Leak Monitor. It provides real-time visibility into code access and transfer events, continually scans for anomalies in code access and transfer, alerts to attempted exfiltration of code, and monitors code channels including file sharing platforms and dev tools for unauthorized import or export.
Finally, Archipelo creates a historical record of coding events for all commits, pull requests, and releases, packaging into an auditable Code Digest. Code digests contain an enhanced, validated, NIST 800-218 compliance SBOM that includes your developer’s attestations.
Archipelo was started by Matthew Wise (Cisco, Bionic) and Dom Sagolla (Twitter, Square, Adobe), and has raised funds from Dell Technologies Capital, Andy Bechtolsheim, Eric Yuan, Gil Penchina, Nima Capital, Samsung, 10X Capital, and Bill Tai.
6.2: Oxeye Security: Delivering Only “True Positives” With App Sec Remediation.
The biggest issue with application security is noise.
Whether the tool is providing Software Composition Analysis, Static Application Security Testing, Dynamic Application Security Testing, or Penetration Testing, the vendors that lead these categories deliver solutions that generate 1000s of alerts. Eventually, organizations become numb to the exposure, either ignoring the warning, or side stepping the security solution.
Oxeye Security eliminates the noise and false positive problem with app sec by delivering a platform that models an application’s run time, and then leverages that intelligence to execute a variety of application security tests simultaneously. Oxeye’s engine correlates alerts from across all of the tools and then validates potential issues by re-running additional tests. Ultimately, only issues that have been validated from multiple perspectives and have a traceable vulnerability flow are surfaced.
As Oxeye’s correlation reaches further into environments across development, test, and production, their intelligence grows reducing false positives to only having true positives!
True positives are routed to the appropriate audience for resolution, whether it is a developer, DevOps, cloud engineer, or application security engineer.
Oxeye was started by Ron Vider and Dean Agron out of Tel Aviv. They have raised funds from Dell Technologies Capital, Intel Capital, More VC, Stonemill Ventures, i3 Equity Partners, and Merlin Ventures.
6.3: AppMap: Shifting ALL The Way Left - Identifying Security Issues While Developers Work In Their IDE, Version Control System and DevOps Tools.
Organizations spend a significant amount of their APM and application security budget on solutions that execute within test environments, staging, or production.
Identifying issues tied to bad code costs significantly more if those issues are found after the developer has committed code into the code base. This expense happens in a number of ways:
Feature velocity stalled due to dev interrupts from new issues.
Large observability platforms drive up to 30% of infrastructure spend with large license fees.
Runtime security solutions tend to require large staging environments with long execution windows to uncover issues.
Most issues discovered in production require code changes to fix (see point #1).
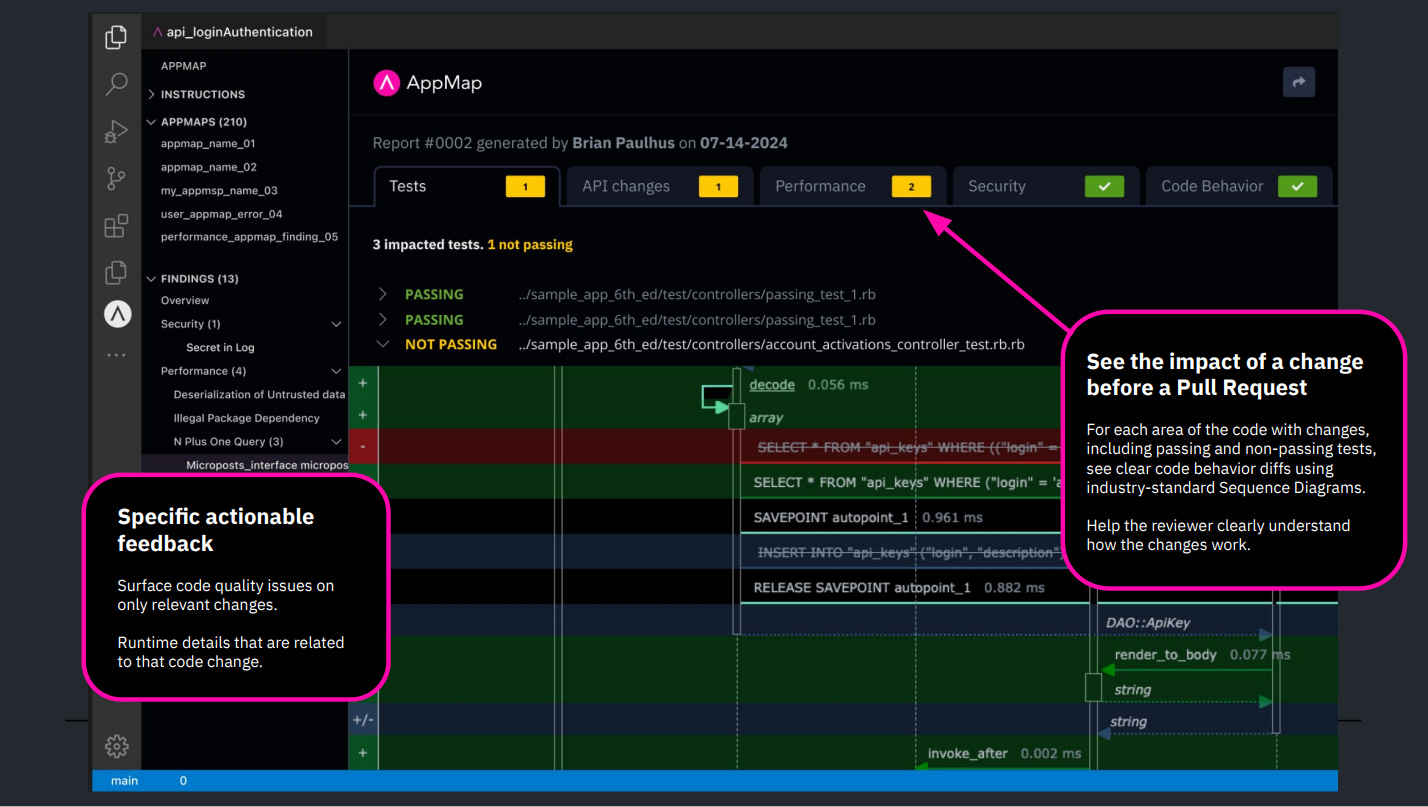
AppMap delivers observability and security runtime insights from within the environments that developers work: within their IDE, version control system, and CI/CD tooling.
AppMap provides a no-instrumentation, no-logging, no-data-exported-to-vendors approach to understanding the application while it is being built. They are able to visualize the dependencies of any application, follow all of the interactions within the system, and trace the flow of data in the implementation.
As a result, AppMap is able to resolve 75% more security and performance issues before the pull request. And when AppMap is deployed within the tools of all team members, it correlates a broad array of application behavior that can block builds / releases where the probability of performance or security issues are likely to materialize as the application shifts right towards production.
AppMap was founded by Elizabeth Lawler and Kevin Gilpin. They are used by 50K developers and have 600K hooks into applications where they are driving insights. They were a finalist at the most recent Techcrunch Disrupt startup competition and have raised VC from a variety of dev-focused investors including Work-Bench, Argon Ventures, Dell Technologies Capital, Unusual Ventures, Venture Guides, and Forgepoint Capital.
6.4: Bastion Zero: Applying Least Privileged Developer Access With Zero Trust IAM.
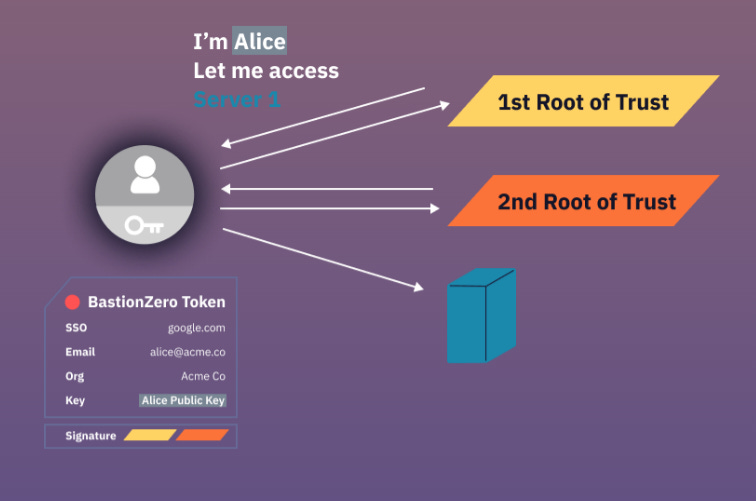
BastionZero delivers zero trust access without creating a single point of compromise. They are able to give developers access to development resources without requiring passwords, VPNs, or SSH keys. This is an experience nirvana for developers who have long had to deal with complicated key management to establish SSH sessions on remote servers or to operate over bandwidth unfriendly VPN connections.
They are able to entirely displace VPN architectures with a double verification protocol that came out of years of distributed architecture and cryptography research. BastionZero has a CLI that sits on your developer’s laptop, the BastionZero cloud service and an agent that sits on your targets. Identity is pulled from a corporate provider for SSO. Key to BastionZero is that their cloud service does not store or control any credentials to your targets (SSH keys, server passwords, IAM roles)
BastionZero was founded by Sharon Goldberg and Ethan Heilman who both were extensive researchers on distributed systems at Boston University. They were 2nd place at the most recent RSA Innovation sandbox, and have raised VC from Dell Technologies Capital, Akamai, and Digital Garage.
6.5: Endor Labs: Software Composition Analysis Without The False Positives - Prioritizing Only Reachable Vulnerabilities In 3rd Party Code.
95% of the vulnerabilities are found in transitive open-source dependencies - the software packages automatically pulled in by the open-source software developers select. Traditional SCA tools have no visibility into these and offer no way to prioritize them beyond severity.
Endor Labs provides a OSS Governance solution that enables better selection of dependencies, prioritizes reachable vulnerabilities for resolution, and creates a deep graph understanding of your entire dependency chain. They also manage 1st and 3rd party SBOMs and generate automated VEX documents which annotate vulnerabilities based upon reachability analysis. They do this by investing heavily in program analysis and call graph technologies, which allow a deep understanding of code behavior.
Endor Labs was started by Varun Badhwar (Palo Alto Networks, Redlock, Salesforce) and Dimitri Stiliadis (Palo Alto Networks, Alcatel Lucent). They have raised funds from Dell Technologies Capital, Lightspeed, and over 40 CEOs, CISOs and CTOs of leading organizations worldwide. Within 8 months of the company's launch, Endor Labs has already been recognized as a Gartner Cool Vendor and became the first company to ever be a finalist in both RSA Conference's Innovation Sandbox, and Black Hat's Startup Spotlight Competition.
6.6: Cequence: Unified API Protection At The Pace Of DevOps.
Cequence is one of the largest API security providers with a discover, comply, and protect approach. They are protecting over 6 billion API calls daily in significant environments including those at Verizon, American Express, T-Mobile, and RBS.
Their solution is able to identify known and unknown APIs, creates a complete API attack surface of an organization, ensures that APIs comply with security test requirements, and blocks API threats in real time. Their unique approach incorporates real time scanning for multiple types of risk that span across every phase of the API lifecycle from development through production.
Cequence was founded by Ameya Talwalkar and Shreyans Mehta, and have received investment from Dell Technologies Capital, Shasta Ventures, HP Pathfinder, Prosperity7 Ventures, Menlo Ventures, T-Mobile, Triplepoint, and Telstra.
6.7: OpsMx: Secure Software Delivery With Delivery BOMs And Deployment Firewalls.
OpsMx has evolved its progressive and continuous delivery engine to a real-time compliance verification platform. With Continuous Delivery providing a last line of defense between assets moving from pre-production into production, organizations can extend their current pipeline automation infrastructure with software supply chain security checks, enforcement, and traceability.
OpsMx has introduced the concept of a Delivery BOM which provides a comprehensive accounting of all the security, compliance, and validation actions taken as part of a specific deployment. When combined with their Deployment Firewall, organizations obtain an auditable and enforceable last line of defense to ensure that only systems that have passed all security elements move into production.
OpsMx was founded by Gopal Dommetry and has raised VC from Dell Technologies Capital, Foundation Capital, Bosch Ventures, Tau Ventures, Emergent Ventures, and EVO Ventures.
7.0: The Investment Landscape For DevOps Is Shifting Around Platform Consolidation, Security Influenced Development, And Automation.
So what, Tyler, is this the end of DevOps? What are the opportunities that you see and how has your investment thesis evolved?
A few thoughts:
We’re seeing a cultural shift from the developer influencer buyer to management as companies belt tighten and spend more on automation and security and less on dev productivity.
As budget belts tighten, dev-focused tools and companies are feeling the crunch. Spend increases on developer-led technology has slowed for the 1st time since 2009.
There hasn’t been the 500-company mass extinction event that I projected last year, but there have been the largest number of acquihires made in the past year.
Developer productivity remains important, but solutions that improve velocity just as easily cause developer friction as they do faster releases, with the complexity of the tool chain hindering as much as helping.
Netting it out - the developer-led landscape is facing three major opportunities:
Consolidation to eliminate toolchain complexity and to harmonize the velocity of releases.
Automation to eliminate the tedious, repetitive elements of software development. While this may be AI development, it’s really a major march towards autonomous development led as much by low-code platforms as GitHub Copilot.
Secure Software Supply Chain solutions due to the ever increasing development complexity alongside increasing mandates and regulations. This market is already generating $2.14B ARR and will triple before the end of the decade.
I think it’s going to be interesting times for CISOs, R&D, investors, and founders.



















Such an awesome report, I've learnt a lot. 🙏 Thanks